
- This event has passed.
The 3rd Session of Trustworthy Biometrics Webinar was Successfully Concluded
July 28, 2021 @ 3:00 pm - 5:00 pm
On July 28, 2021, the 3rd Session of Trustworthy Biometrics Webinar was successfully concluded, which was hosted by the IEEE Beijing Section Biometrics Council Chapter and organized by NiCE team from the Center for Research on Intelligent Perception and Computing of the Institute of Automation, Chinese Academy of Sciences. This report invited Vincenzo Piuri, chairman of IEEE Systems Council and professor of the University of Milan, Italy, and Dr.Yufei Han, senior research scientist of the Institut national de recherche en informatique et en automatique(INRIA), as keynote speakers to give a report on the themes of “Artificial Intelligence for Biometric Technologies and Systems” and “Attackability Evaluation of Machine Learning Models with Categorical Input” respectively. More than 600 viewers participated in this event on online conferences and live streaming platform.

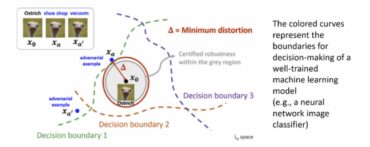
Although great progress has been made in avoiding attacks on continuous data (such as images and videos), how to design adversarial samples for discrete data is still a rarely studied but important problem.

Discrete data widely exists in real-world applications, designed by analysts for financial fraud detection, spam detection, gene analysis in bioinformatics and malware dynamic analysis. Many of these applications are critical links of security, and these applications are also eager to deploy machine learning technology. Therefore, in these industrial practices, the adversarial vulnerabilities of discrete data must be investigated.
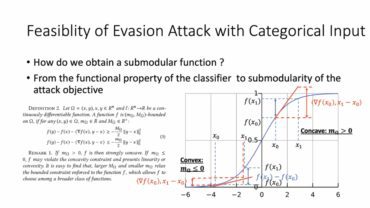
In essence, designing adversarial modification of discrete data is a NP hard combinatorial optimization task. Similar to the problem in continuous domain, the solvability of avoiding attack task on discrete data (also known as attackability) is closely related to the characteristics of attack target and target classifier.
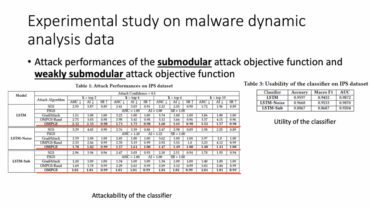
Therefore, Dr. Yufei Han started from “What conditions should an attack target meet to define a solvable attack problem?” “Can we provide provable attackability?” , introduced in detail the attackability measurement of white box evasion attack using submodularity theory on nonlinear classifiers of discrete data (such as deep neural network). In addition, he and his team also proposed an effective and provable heuristic search method for discrete inputs evasion attacks.

Professor Vincenzo piuri introduced the application of biometrics in various fields and the correlation of artificial intelligence (especially neural network and deep learning), and analyzed various problems and prospects of artificial intelligence in these applications.
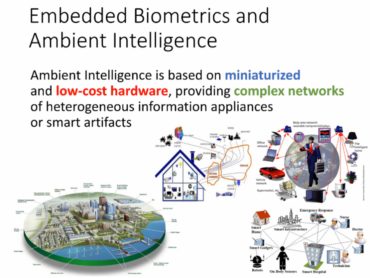
Biometrics studies automated methods for identifying individuals by measuring one or more physical or behavioral characteristics. Certain human physiological characteristics or behaviors are specific characteristics that can be uniquely associated with a person. Retinal, iris, DNA, fingerprint, palmprint or finger length patterns are typical physical characteristics unique to individuals. In addition, voiceprint, gait or handwriting can also be used for this purpose.

Nowadays, biometrics technology is developing rapidly. This science is becoming more and more accurate in identifying people and behavior. As a result, these technologies are becoming increasingly attractive and effective in key applications, such as creating secure personal IDs, controlling access to personal information or physical areas, identifying terrorists or criminals, researchers’ movement, and monitoring human behavior.
Using biometrics in real life usually requires very complex signal and image processing and scene analysis, such as biometric extraction and recognition, personal tracking, face tracking, eye tracking, activity / living body detection and facial expression recognition.
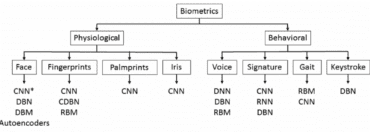
Artificial intelligence technologies (including neural networks, fuzzy logic, evolutionary computing and multi-agent systems) have been proved to be useful and effective in solving such data processing task, especially when it is difficult to identify algorithms and there are sufficient descriptive examples, when fuzzy description more naturally captures the essence of the problem, or complex nonlinear optimization is required, or multiple agents work together to solve application problems.
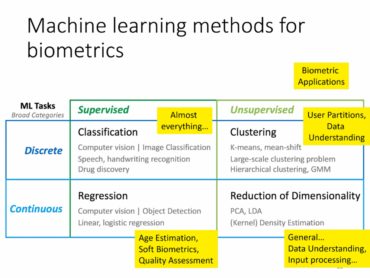
With more diverse applications of biometric recognition used in our daily life, people pay more and more attention to the security and credibility of biometrics. Many new problems, such as deepfake and adversarial attack, pose new threats to the existing biometric technology. Therefore, with the support of IEEE Beijing Section Biometrics Council Chapter, we planned the Trustworthy Biometrics Webinar, which provides an international exchange platform for scholars at home and abroad who pay attention to biometrics security.
Finally, We sincerely thank the teachers and students who participated in this online activity, we hope you can continue to support and pay attention to our subsequent series of activities. We welcome more people from all over the world to join us and explore more reliable biometric technology in the future.
